Secure Delaware CTF: External Pentest Writeup
By: Charles Adams
CEO & Co-Founder at Exploit Strike | Offensive Security Professional | Helping Businesses Stay Secure with Penetration Testing | Marine Corps Veteran
October 30, 2024
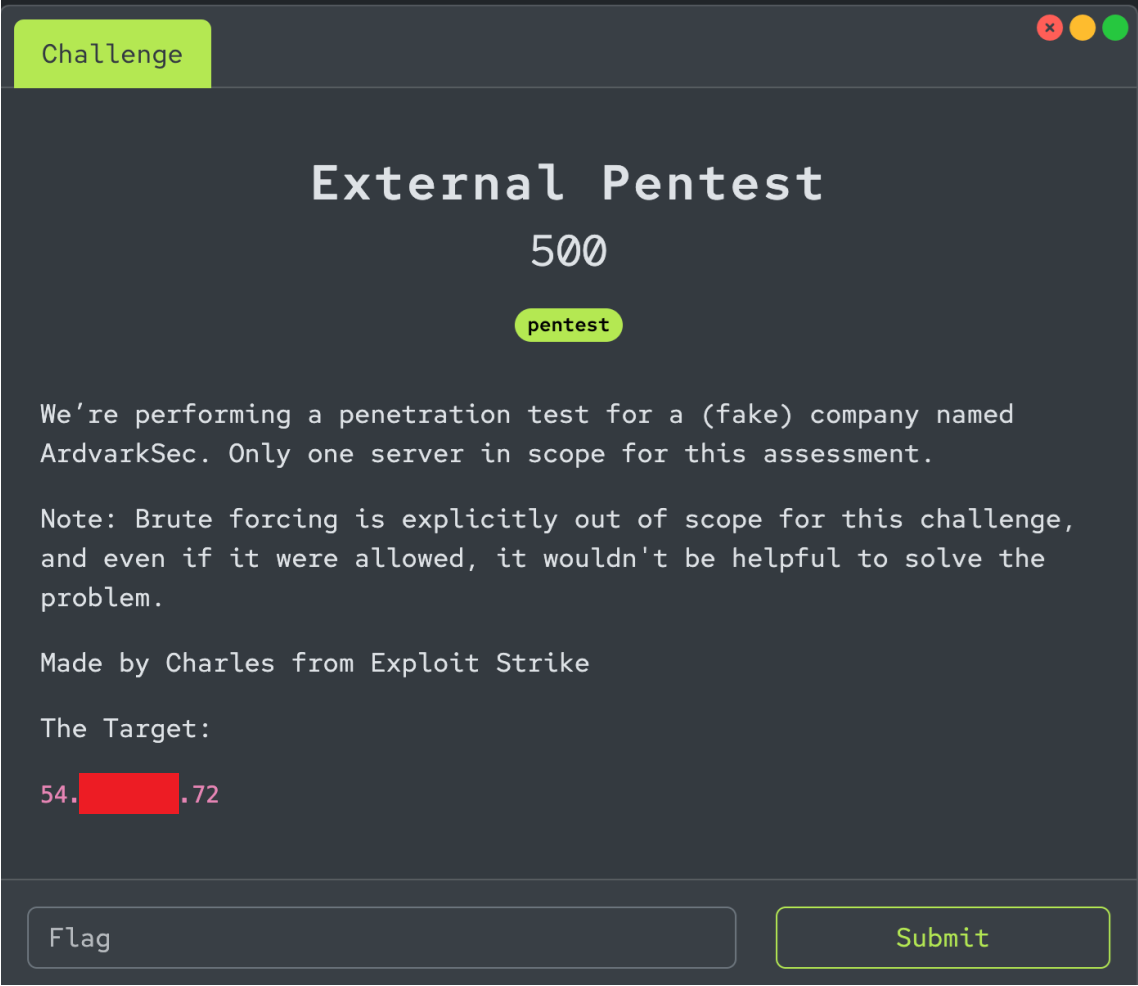
Problem Description
You are presented with a web application hosted by a (fake) company called ArdvarkSec. The application contains a login page that sets cookies based on the user’s authentication status. Your goal is to gain access to the admin interface and retrieve the flag.
Step 1: Analyze the Page
Upon visiting the page, you notice there is a login form requiring a username and password. You try admin:admin with no luck.
Step 2: Inspecting the Cookie
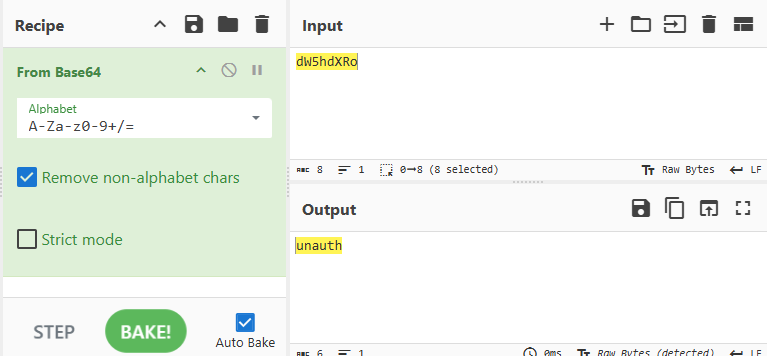
The first step is to inspect the cookie value that was set. You can do this by using the browser's developer tools. Here, you find that the auth cookie is set to:
Now you inspect the network traffic with Chrome's developer tools and find the 'auth' cookie has been assigned. Intuition tells us it's encoded in base64.
Using a simple command in the terminal (echo dW5hdXRo | base64 -d), you find that the value is `unauth`, which indicates that you are currently not authenticated.
You can also use CyberChef, a super helpful data manipulation tool to encode/decode date.
Step 3: Cookie Manipulation
Since the cookie value is simply Base64-encoded, you can try changing it 'user' or 'admin' to see if you can gain access. You decide to encode the word `admin` in Base64. Running echo -n admin | base64 gives the encoded value:
Or use CyberChef to get the base64 encoded admin cookie value:
Step 4: Setting the Cookie
Next, you use Postman to modify the auth cookie value to YWRtaW4=. After refreshing the page, you see a different message indicating successful login as the admin.
Step 5: Flag Retrieval
With the auth cookie set to admin, the page shows a welcome message for the admin user, and you can retrieve the flag displayed on the page:
Step 6: Lessons Learned
Cookie Manipulation: The key to solving this challenge was understanding the use of cookies and how they could be manipulated.
Base64 Encoding: The authentication mechanism relied on Base64-encoded values, which are easily decoded and manipulated.
Web Security Issues: Relying solely on cookies for authentication without proper encryption or validation is a major security flaw, which allowed an attacker to easily escalate privileges.
Summary
This challenge demonstrates how weak authentication mechanisms, such as using Base64-encoded cookies without further verification, can be exploited to gain unauthorized access to sensitive areas of a web application. It highlights the importance of secure cookie handling, proper encryption, and avoiding the use of predictable encoded values for sensitive information.
Here are some other CTF writeups by Charles: https://caadams4.github.io/cyberblog/
Looking forward to seeing you next year at Secure Delaware!